OpenClaw Can Transform Your Business… If It Doesn't Compromise It First

There's a new AI tool making the rounds that has the tech world genuinely excited. And genuinely worried. It's called OpenClaw (you might have also seen it called Clawdbot or Moltbot; it's been through a few rebrands in the span of weeks). It's an open-source AI agent that runs on your machine, reads your email, manages your calendar, automates workflows, and takes action across the tools you already use.
It actually works. And that's exactly why you need to read the rest of this post.
"I Already Let ChatGPT Access My Google Drive. How Is This Different?"
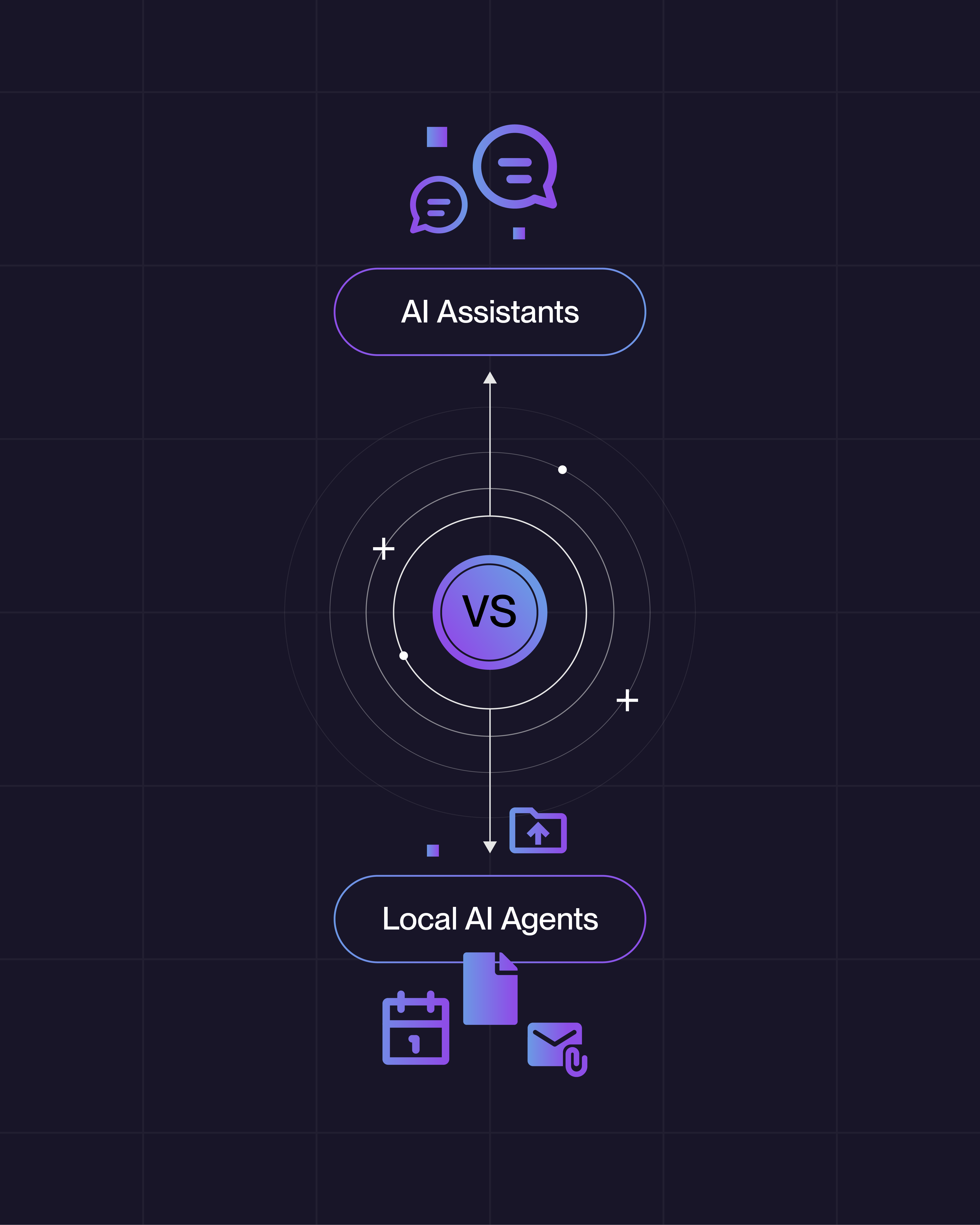
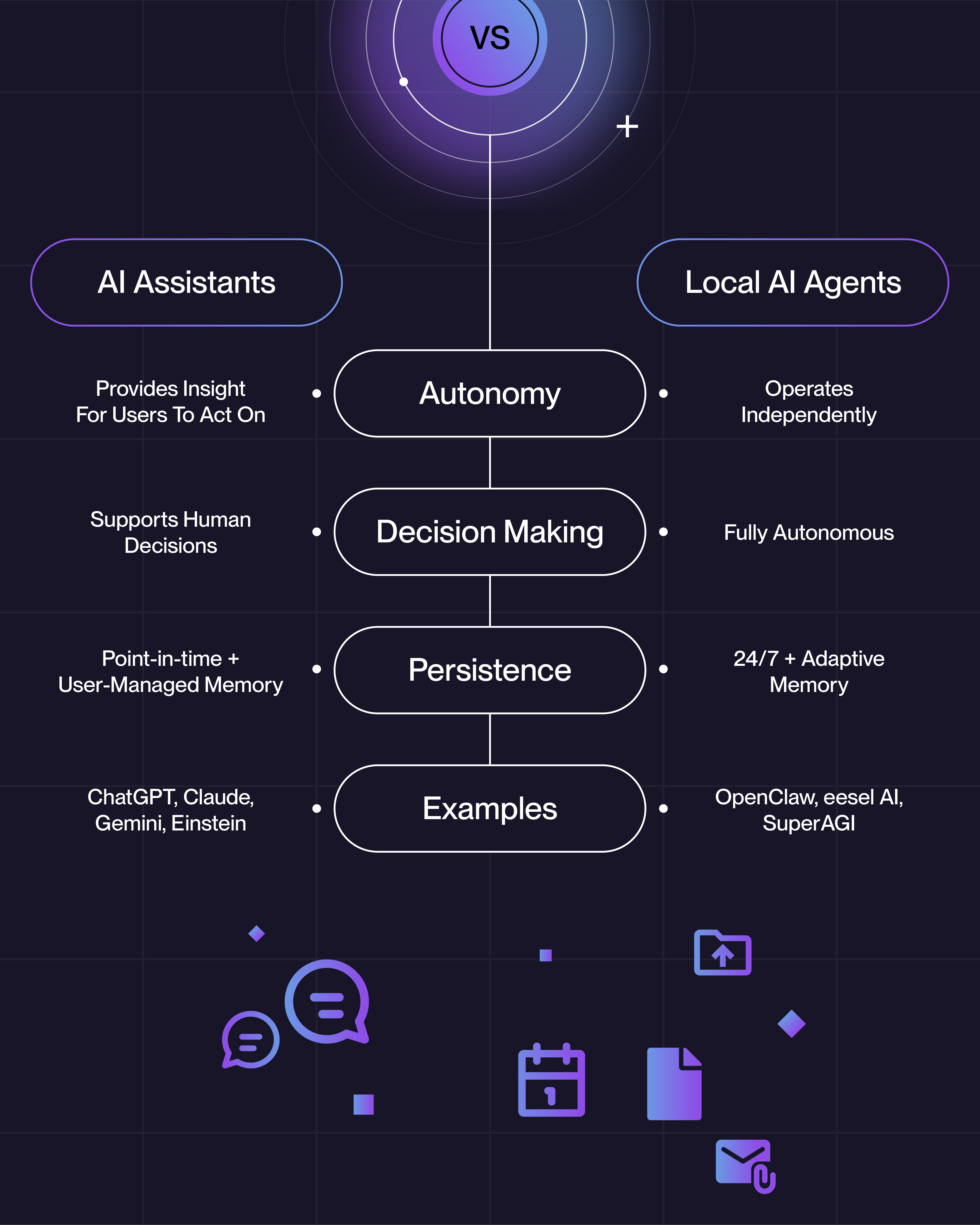
Fair question. When you connect ChatGPT, Claude, or Gemini to your Google Drive, you're opening a controlled, momentary window. You ask it to look at a document, it looks, it responds, and the session ends. Point-in-time access. The companies behind those tools spend tens of millions of dollars on security engineering to keep those windows safe.
OpenClaw is a fundamentally different animal. It doesn't connect for a moment, it lives on your machine. It runs 24/7. It has persistent memory, meaning it remembers everything it's seen across every session. It reads your emails, Slack messages, and files continuously, not on-demand. It can execute shell commands, run scripts, and take actions on your behalf around the clock. Even when you’re not looking.
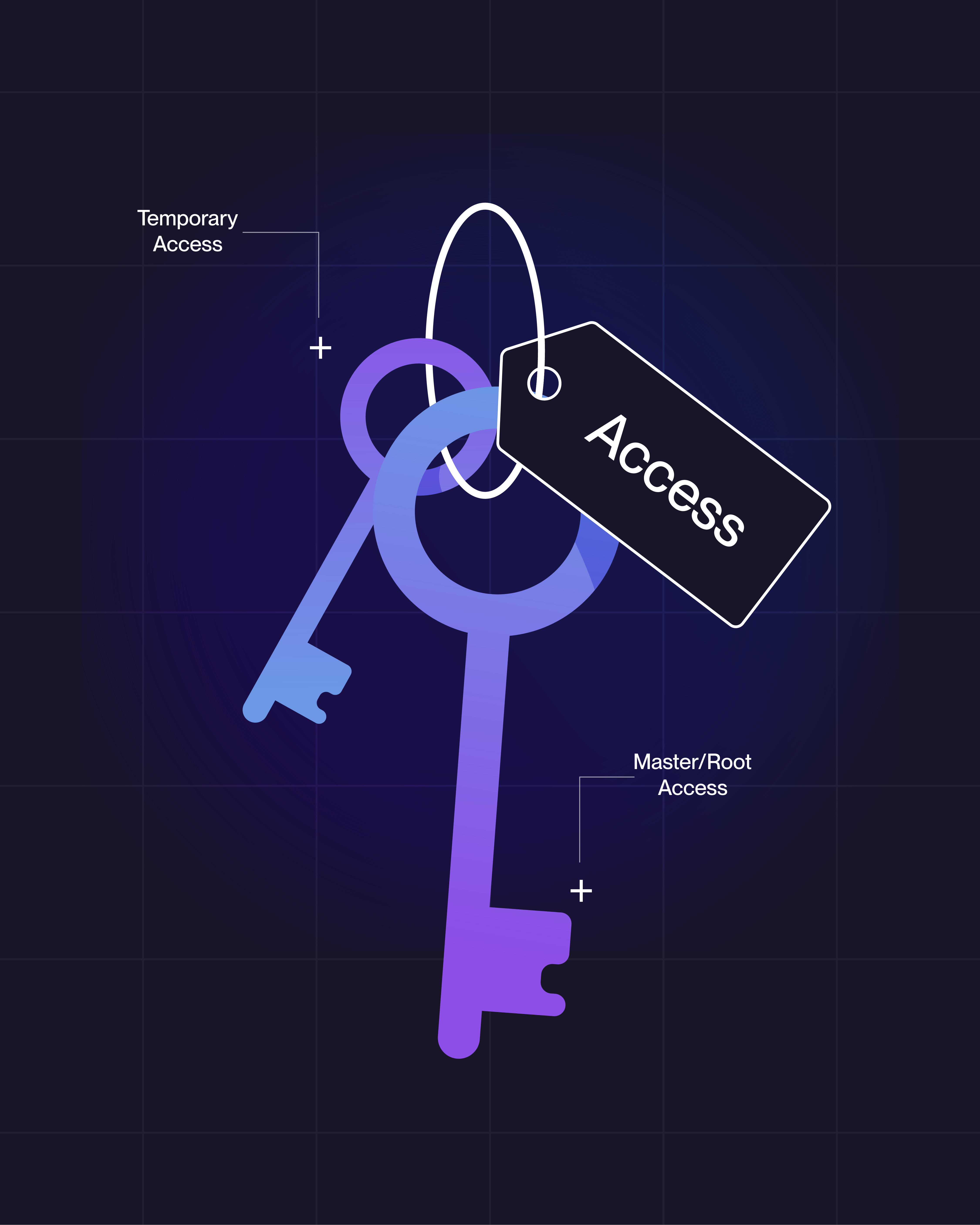
Think of it this way: using ChatGPT with your Drive is like handing a contractor a key to one room for an afternoon. Installing OpenClaw is like giving a stranger a master key to the entire building and telling them to move in.
The ambition behind OpenClaw is the same as the big players. The security posture is not. This is an open-source project that went viral practically overnight. The community is passionate, the creator is responsive, and improvements are shipping fast. However the security surface is still being actively discovered, sometimes by the good guys, sometimes not.
The Bad Actors Are Already Here
Let’s talk about the bad guys. This isn't a scare-tactic section I wrote with hypothetical risks. Everything below has already happened. Most of it in the last two weeks. So hold on to your butts, but keep reading after the scary part.
Poisoned Skills That Look Legitimate
OpenClaw extends its capabilities through "skills", downloadable packages available on a marketplace called ClawHub. In theory, this is great. In practice, a recent security audit of roughly 2,900 skills on ClawHub found over 340 of them were malicious. They had professional documentation, believable names like "solana-wallet-tracker" and "youtube-summarize-pro," and they worked exactly as advertised. They also quietly stole credentials, installed keyloggers, and opened backdoor access to your machine in the background.
Worse, attackers are gaming the popularity rankings to get malicious skills to the top of the list. Who can publish a skill to this marketplace? Anyone with a GitHub account that's at least one week old.
Your Inbox Becomes an Attack Vector
Because OpenClaw continuously reads everything coming in (emails, Slack messages, text messages), a carefully crafted message from someone else can manipulate what the agent does next. Security researchers call this prompt injection, and it's an industry-wide unsolved problem. But OpenClaw's persistent memory makes it uniquely dangerous.
Here's why: a poisoned instruction hidden in an otherwise normal email doesn't have to trigger immediately. It gets absorbed into the agent's memory. Weeks later, when the agent retrieves that memory fragment in the right context, the payload activates and your data starts leaving through a door you didn't know was open. Yup, we’re talking real-life sleeper agents and trigger words.
Accidental Front-Door Exposure
OpenClaw includes a web-based control panel for managing your agent. Misconfiguration, which is remarkably easy to do, can expose that panel to the public internet, complete with your API keys, conversation history, and connected service credentials sitting there in plain text. Researchers have already found live instances wide open to the world.
And just this week, a critical vulnerability (CVE-2026-25253) revealed that even properly configured "localhost-only" setups could be fully compromised by a single malicious link. One click, and an attacker has operator-level access to your entire agent. Including the ability to disable its safety guardrails and execute code on your machine. It takes milliseconds.

So Should You Avoid It Entirely?
No! And that's the important part.
The architecture behind OpenClaw (local AI agents with persistent memory, tool access, and cross-platform integration) is genuinely the future of business automation. Imagine an AI that actually knows your business context, coordinates across every tool your team uses, and gets smarter over time. That's not science fiction. That's what OpenClaw is demonstrating right now.
When properly configured and secured, systems like this can automate repetitive workflows, act as institutional memory for your organization, and deliver measurable productivity gains almost overnight. The concept isn't the problem. The wild-west, DIY approach to deploying it is.
The Smart Play
The answer isn't "stay away." The answer is "don't go it alone."
Don't install skills blindly. Every skill should be reviewed line-by-line by someone who knows what they're looking for before it touches your system. Or better yet, have your skills written from scratch for your specific needs.
Don't configure it yourself unless you genuinely understand network security, containerization, and credential management. The defaults are not secure. The documentation says so itself.
Don't treat "it runs on my machine" as a security strategy. Your machine is connected to the Internet. Your agent reads content from the internet. "Local" does not mean "safe." In fact, it can mean the opposite.
Do treat this like the powerful infrastructure it is because that's exactly what it is. You wouldn't set up your own server room without professional help. This deserves the same respect.
We Can Help
Shameless plug time! At Purple, Rock, Scissors, we're already helping clients navigate this space. Evaluating agent architectures, auditing skills and configurations, and building secure implementations that deliver the productivity gains without the exposure. We'll be publishing a deeper technical white paper on this topic later this week for those who want the full picture (and we’ll focus more on the positive side, I promise).
If your team is exploring OpenClaw or similar AI agent tools, talk to us before you install anything. A conversation now is a lot cheaper than a breach later.
